Alert & Warnings
Warning: New Threats Ransom Ware Please Read!!!
Patch you Window's PC Now! Remove Window's Xp PC's if possible, or upgrade
to a newer version of Windows if possilbe.
Old 2017 Threats WannaCry / WannaCrypt *Golden Eye / Petya / NotPetya as of June 27th 2017
Global Cyber attacks are launched around the clock 24/7 averaging 4+ Million per day!
-Take a look at a Live Cyber Attack Threat Map!
-Take a interactive look at a Live Cyber Defense Kaspersky Threat Map!
New Threats as of 2016-2017.
Warning: Crital Alerts;
With new data breeches and Account Passwords being stolen, you
should check up on your accounts. Have you been owned i.e. pwned?
(Your Password-owned by someone else?)
Read New Threat as of 2016-17 below!
The World is in your hands via the Internet, aka., WWW (The World Wide Web).
Since you are on the web you should know some thing about the Technology you are using.
WWW ( World Wide Web aka The Internet explained in 40 Maps)
since you are on our web site. As part of our ministry to you, It just makes sense to us to alert you of Alerts & Warnings.
These alerts are not to generate fear, but as an advisory, and to help in equipping you for safer internet surfing.
Remember:
*No weapon that is formed against thee shall prosper; and every tongue that shall rise against thee in judgment thou shalt condemn. This is the heritage of the servants of the Lord, and their righteousness is of me, saith the Lord. Isaiah 54:17 Psalm 91:1-3.
*And the Lord said, If ye had faith as a grain of mustard seed, ye might say unto this sycamine tree, Be thou plucked up by the root, and be thou planted in the sea; and it should obey you.
Luke 17:6
Note: Should fear try and over take you after reading this alert, read No Fear Here! .
Note: Scripture verses and other links provided on this page will take you to other sites,
use your back button to get back to us or, right click / press and hold on the link to open in a new tob or window.
use your back button to get back to us or, right click / press and hold on the link to open in a new tob or window.
New Threat as of 2016-2017.
Warning: Crital Alerts;
Have you been owned i.e. pwned?
Have you been Gooliganed?
Cyber Attacks and Breached web sites and accounts are quickly becoming the norm.
With:
You should be aware if your account might have been hacked. Here's a web site service that can help you check and see if your account have been
compromised (By way of OPENDNS).
Just click the link "Have I Been pwned?" type in your e-mail account(s) to see if it has been compromised
If so login to your account and change your password. Sites that have been pwned. (WARNING: There are sites listed that we definitely do not condone or support, please be aware it it not our listing).
It is a long list but well worth looking at, you might see one of your hang-outs/sites listed.
If so:
Time for a clean operation system installation on your mobile device is required.
Time to login to your account and change your password.
**Cyber Attaks (DDoS attacks) are launched by the millions every day take a look at Actual Live Attacks. (Note may load slower on some ios devices).
If you are curious to about what certain Viruses and worms do click ThreatExpert
Need to learn more about Password security click here.
Warning: Crital Alerts;
Have you been owned i.e. pwned?
Have you been Gooliganed?
Cyber Attacks and Breached web sites and accounts are quickly becoming the norm.
With:
- Android Gooligan Malware (Nov-Dec 2016) Compromises 1Million + Google Accounts
- Mirai Variant (Nov 2016) Leaves 5 Million Modems Vulnerable Worldwide
- Yahoo recently (Sep 2016) reporting 500 Million account passwords breached/stolen
You should be aware if your account might have been hacked. Here's a web site service that can help you check and see if your account have been
compromised (By way of OPENDNS).
Just click the link "Have I Been pwned?" type in your e-mail account(s) to see if it has been compromised
If so login to your account and change your password. Sites that have been pwned. (WARNING: There are sites listed that we definitely do not condone or support, please be aware it it not our listing).
It is a long list but well worth looking at, you might see one of your hang-outs/sites listed.
- Have I been Gooliganed?
If so:
Time for a clean operation system installation on your mobile device is required.
Time to login to your account and change your password.
**Cyber Attaks (DDoS attacks) are launched by the millions every day take a look at Actual Live Attacks. (Note may load slower on some ios devices).
If you are curious to about what certain Viruses and worms do click ThreatExpert
Need to learn more about Password security click here.
New Threat as of April 27th, 2014.
Warning: Crital Alerts;
Zero-Day exploit Reported, Affects Internet Explorer Versions 6-11 !
Critical Alert for Zero-Day Reported, Affects Internet Explorer Versions 6-11 !
A new zero-day flaw is being reported that affects Internet Explorer versions 6 through 11, with IE9 through IE11 being actively targeted. When enacted, the vulnerability has the potential to take over the computer. And depending on how high the rights level of the user, will determine how much damage can be done.
In other words, if a user has administrative rights to the computer, the exploit will enjoy full control. When setting up a pc, administrative rights for normal users is a no-no, if normal users already have administrative right they should be down-graded. Cases like this should be enough to convince user/management to revoke administrative rights for users, and across the board in business usaged..
MSN News Coverage
US-CERT To Be updated
CERT To Be updated
* Microsoft Security Advisory To Be updated + Things you can do!
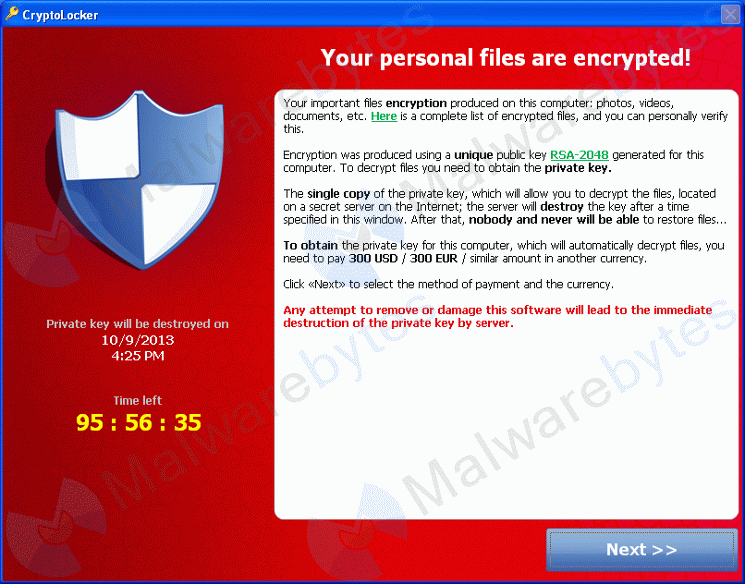
Critical Alert for CryptoLocker !
From Wikipedia, the free encyclopedia (Redirected from Cryptolocker) Jump to: navigation, search CryptoLocker Classification Trojan horse Type Ransomware Subtype Cryptovirus Operating system(s) affected Windows.
CryptoLocker is Trojan horse malware which surfaced in late 2013, a form of ransomware targeting computers running Microsoft Windows. CryptoLocker disguises itself as a legitimate attachment; when activated, the malware encrypts certain types of files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware's control servers. The malware then displays a message which offers to decrypt the data if a payment (through either Bitcoin or a pre-paid voucher) is made by a stated deadline, and says that the private key will be deleted and unavailable for recovery if the deadline passes. If the deadline is not met, the malware offers to decrypt data via an online service provided by the malware's operators, for a significantly higher price in Bitcoin.
Although CryptoLocker itself is readily removed, files remain encrypted in a way which researchers have considered infeasible to break. Many say that the ransom should not be paid, but do not offer any way to recover files; others say that paying the ransom is the only way to recover files that had not been backed up.
Ok so What's the bottom line check the links below?
(From: SOPHOS)
(From: US-CERT)
Warning: Crital Alerts;
Zero-Day exploit Reported, Affects Internet Explorer Versions 6-11 !
Critical Alert for Zero-Day Reported, Affects Internet Explorer Versions 6-11 !
A new zero-day flaw is being reported that affects Internet Explorer versions 6 through 11, with IE9 through IE11 being actively targeted. When enacted, the vulnerability has the potential to take over the computer. And depending on how high the rights level of the user, will determine how much damage can be done.
In other words, if a user has administrative rights to the computer, the exploit will enjoy full control. When setting up a pc, administrative rights for normal users is a no-no, if normal users already have administrative right they should be down-graded. Cases like this should be enough to convince user/management to revoke administrative rights for users, and across the board in business usaged..
MSN News Coverage
US-CERT To Be updated
CERT To Be updated
* Microsoft Security Advisory To Be updated + Things you can do!
- Do Not use Microsoft Internet Explorer Vers 6-11. Use Firefox or Chrome.
- If you must use Micosoft Internet Explorer Turn off Flash add one i.e. "Shockwave"
Disabling the Flash plugin within IE will prevent the zero-day exploit “Operation Clandestine Fox” from functioning, As the attack will not work without Adobe Flash Instructions for disabling Internet Explorer before turning off that Flash is work by clicking on the Adobe Flash link below you should see a test animation when it it working correctly. After the add on is disabled test the Adobe Flash link below again do not reinstall or enable shockwave until Microsoft has issued a fix. - Adobe Flash Test Link. ( http://helpx.adobe.com/flash-player.html )
iE 7-8
Tools >>> Internet Options >>> Program Tab >>> Manage add-on options button >>> Filters >>> Add-ons that run without requiring permission >>> Select Shockwave Object >>> Click Disable button at bottom
iE 10-11
Tools >>> Internet Options >>> Program Tab >>> Manage add-on options button >>> Select Toolbars and Extensions >>> Under the “Show:” Drop Down menu Select All Add-ons >>> Select Shockwave Object >>> Click
- If you must use Micosoft Internet Explorer Turn off Flash add one i.e. "Shockwave"
Critical Alert for CryptoLocker !
From Wikipedia, the free encyclopedia (Redirected from Cryptolocker) Jump to: navigation, search CryptoLocker Classification Trojan horse Type Ransomware Subtype Cryptovirus Operating system(s) affected Windows.
CryptoLocker is Trojan horse malware which surfaced in late 2013, a form of ransomware targeting computers running Microsoft Windows. CryptoLocker disguises itself as a legitimate attachment; when activated, the malware encrypts certain types of files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware's control servers. The malware then displays a message which offers to decrypt the data if a payment (through either Bitcoin or a pre-paid voucher) is made by a stated deadline, and says that the private key will be deleted and unavailable for recovery if the deadline passes. If the deadline is not met, the malware offers to decrypt data via an online service provided by the malware's operators, for a significantly higher price in Bitcoin.
Although CryptoLocker itself is readily removed, files remain encrypted in a way which researchers have considered infeasible to break. Many say that the ransom should not be paid, but do not offer any way to recover files; others say that paying the ransom is the only way to recover files that had not been backed up.
Ok so What's the bottom line check the links below?
(From: SOPHOS)
(From: US-CERT)
|
1). CryptoLocker.
This is a Criminal & Extortionary Weapon. Be Aware $300 Ransom Fee! "This infection is typically spread through emails sent to company email addresses that pretend to be customer support related issues from Fedex, UPS, DHS, etc. These emails would contain a zip attachment that when opened would infect the computer. These zip files contain executables that are disguised as PDF files as they have a PDF icon and are typically named something like FORM_101513.exe or FORM_101513.pdf.exe. Since Microsoft does not show extensions by default, they look like normal PDF files and people open them.When CryptoLocker was first released, it was being distributed by itself. Newer malware attachments appear to be Zbot infections that then install the CryptoLocker infection."
How do I protect myself against ransomware?
"Despite its threatening nature, ransomware is still a type of malware. We recommend the same tips to help keep any malware out of your PC:
If you back up to other usb drives do not leave them connected to your PC. Scan them for virus /malware /ransomware and then store them. CryptoLocker looks for any connected, or mapped drive for data to encrypt, this includes flash & even cloud drives that have been mapped for easy access. This trojan horse ramsomware especially targets businesses with networked shared drives. |
As people order more and more, on line with FedEx, UPS, DHS, USPS ect., and doing online banking.
1. Amazon then provides you a link to check your package shipment status within Amazon. Login to your Amazon account to check it.. 2. Copy the tracking number that Amazon has provided. Go directly to the shippers tracking site and paste their tracking number in at their site. This way you won't be clicking on a email link. Example 2. Banking accounts and other accounts. Always remember; Your bank , and other accounts, know your name. If you receive a message along this line saying and in the body of the message. Dear _______________ Customer we have had a server error and need you to update your data please click the link in this e-mail or open the attachment provided. Do not click or open. this is some sort of attack. Go Directly to your bank's website to do your banking or check your information. It should read something like this Dear Your Name .......
Take a little time and watch these Video(s), at lest the 1st one.
Scammers and attackers educate themselves. You should too! |
Xp
2). End of Life for Windows Xp & Office 2003. 
2014 is Here!
And with it has come the End Life (Support) of Windows Xp in all flavors. Microsoft retired Windows Xp & Office 2003 support and patching on April 8, 2014. Which means any PC running Xp will be open to hacks, malware, spyware, ransomeware, hijacking and other invasions. You need to be prepared, here are some options.
End of Life (Support) for Windows Vista.
End of Life (Support) for Windows 7.
End of Life (Support) for Windows 8.

More Alerts & Warning are on way as soon as they become available.
| ||||||
| Technology Tips |
Home | About us | Events | Healing | Ministry | Prayer | Study | Webmaster | Contact Us| Word of Victory | Salvation | Praise Report